JuicyLightning: A New Product for Event filtering, Account monitoring and Real-Time media asset protection

Today’s online businesses should not only find new channels to attract clients and promote their services, but also protect both customers’ and brand’s existing assets. Following our experience, the toxic or risky traffic proportion estimates around 15-20% to existing customers depending on the degree risk assessment on early stages. As for the new traffic, it varies between 25 and 30%.
Apart from obviously fraudulent traffic with high-risk attributes, there is also a low-quality toxic primary traffic with low conversion rates. In some cases, it may even exceed the company's fraud volume.
In fact, the product helps to prevent online fraud. Every time fraudulent events occur on the client's website or with the personal account, the system activates specific triggers.
The new solution can be used for protection when downloading applications and media assets, as well as providing basic bot filtering against media fraud.
In addition, the solution is suitable for user account monitoring and protection within financial institutions. It keeps classifieds safe and prevent account takeovers via remote access.
JuicyLightning effectively prevents remote access threats and social engineering attacks, such as fraudulent calls, phishing, and credential manipulation. JuicyLightning can also efficiently detect suspicious access attempts to personal accounts and identify linked accounts, helping to track connections between a single user’s multiple accounts.
JuicyLightning tracks high-risk user behavior, such as the use of virtual machines, randomizers, toxic VPNs, or TOR networks, injection attempts, and other technical threats.
Bots represent automated software applications that visit websites or use online services. It’s crucial for companies to recognize bot traffic to protect their resources and ensure the reliability of their online operations.
Click bots are programs that automatically click on ads. They become increasingly popular. Scraping bots can steal content, violating intellectual property rights and damaging brand reputation.
Additionally, setting up bot blocking and detection helps to establish a stronger business’s network and server infrastructure against DDoS attacks and hacking attempts. Bots can account for 20% to 60% of all clicks, negatively impacting return on investment.
Malicious bots can damage website analytics, leading to inaccurate data analysis and poor business decision-making. They utilize server resources and communication channels slowing down the website speed and performance. It results in downtimes and unexpected financial losses.
Click fraud is used to mispresent a company’s organic traffic stats. It happens through display ads, videos, social media, or search, often using anonymous VPNs. This traffic generates zero revenue. What’s more, it may cause companies to leave a compromised promotional channel.
Ad stacking is a common form of mobile fraud, especially in pay-per-click advertising. It involves multiple ads stacked on top of each other. The problem here is that users see ser only the top ad. As a result, advertisers pay for impressions and clicks even though the user never sees the ad.
JuicyLightning also helps with other tasks related to protecting assets in the online environment.
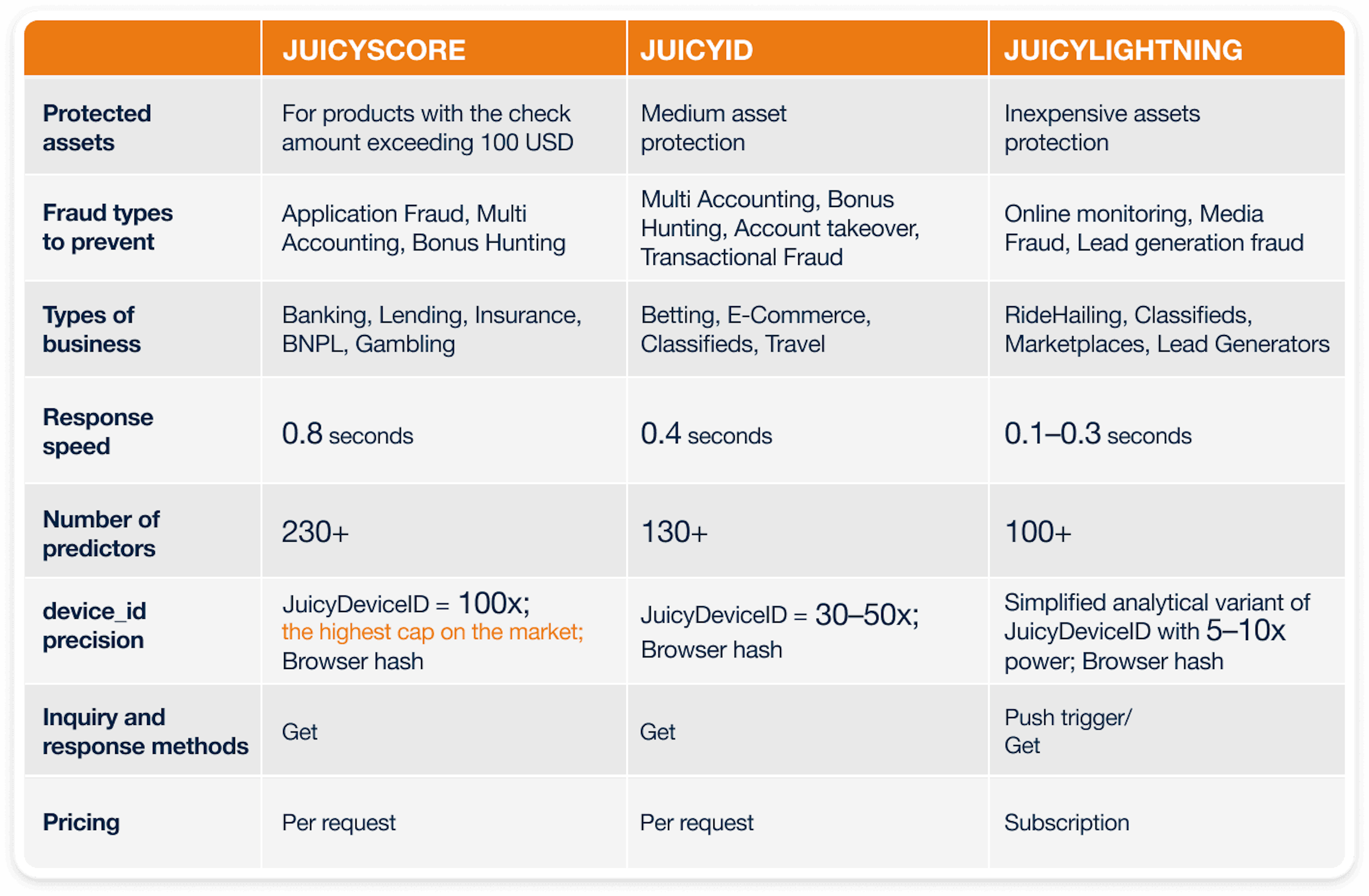
JuicyScore is the core of an advanced anti-fraud solution designed to protect higher-value assets that range from significant bonuses to loans. With this solution, online businesses can significantly reduce application fraud risks, attract new customers, and build trust. JuicyScore allows for segmenting incoming traffic by risk levels, improving the accuracy and efficiency of decision-making systems.
JuicyID is a lighter version of JuicyScore. It is designed to protect online service accounts. The product protects lower-value assets in a fast response time. JuicyID uses Device ID, one of the most reliable digital fingerprints, with a data vector containing 130+ attributes. This allows the system to create various rules to prevent fraud and detect suspicious activity from virtual users while maintaining cost efficiency.
JuicyLightning is a specially developed independent technology designed to filter high-risk events and detect media fraud. It is one of the fastest and most effective solutions on the market boasting a response time between 100 and 300 milliseconds including data delivery time. JuicyLightning also plays a crucial role in combating fraud related to bot traffic.
All three products — JuicyScore, JuicyID, and JuicyLightning — are interconnected and address different fraud prevention tasks. Together, they form a unified ecosystem to deliver high-end protection against various types of fraud and enhance overall security. They can seamlessly utilize each other's data to increase accuracy.
JuicyLightning is a highly effective system when instant responses to red flags are needed. It improves prompt decision-making. In cases of elevated risk, the system triggers back-push events according to their risk level. We present one of the fastest and most effective solutions on the market, which effectively filters out applications showing signs of high risk and commercial fraud, a growing global issue over the years.
Get a live session with our specialist who will show how your business can detect fraud attempts in real time.
Learn how unique device fingerprints help you link returning users and separate real customers from fraudsters.
Get insights into the main fraud tactics targeting your market — and see how to block them.
Phone:+971 50 371 9151
Email:[email protected]
Our dedicated experts will reach out to you promptly