Our Proprietary Online Scoring Technology Unlocks Device ID Intelligence
Leveraging advanced data science, we produce highly reliable scores and comprehensive insights to support your business decisions


Unmatched Stability
A highly stable and consistent digital fingerprint for accurate fraud detection across devices and platforms.

Comprehensive Vectors
Analyzes over 100 attributes for precise fraud detection, all without utilizing sensitive personal or creditworthiness data.

Advanced Fraud Detection
Detects high-risk behavior, virtual machines, browser anomalies, and other fraudulent tactics in real-time.

Customizable Risk Rules
Seamlessly integrates into existing systems, allowing for tailored fraud prevention rules.

Unlock Device ID Intelligence
We empower online businesses to stay ahead with cutting-edge risk management & fraud prevention technologies
Book a Demo65 000 +
parameters collected from every device
220
parameters for device scoring
45 +
countries of presence all over the globe
Utilizing over 65,000 non-personal data points, we generate highly predictive scores and more than 200 credit risk parameters
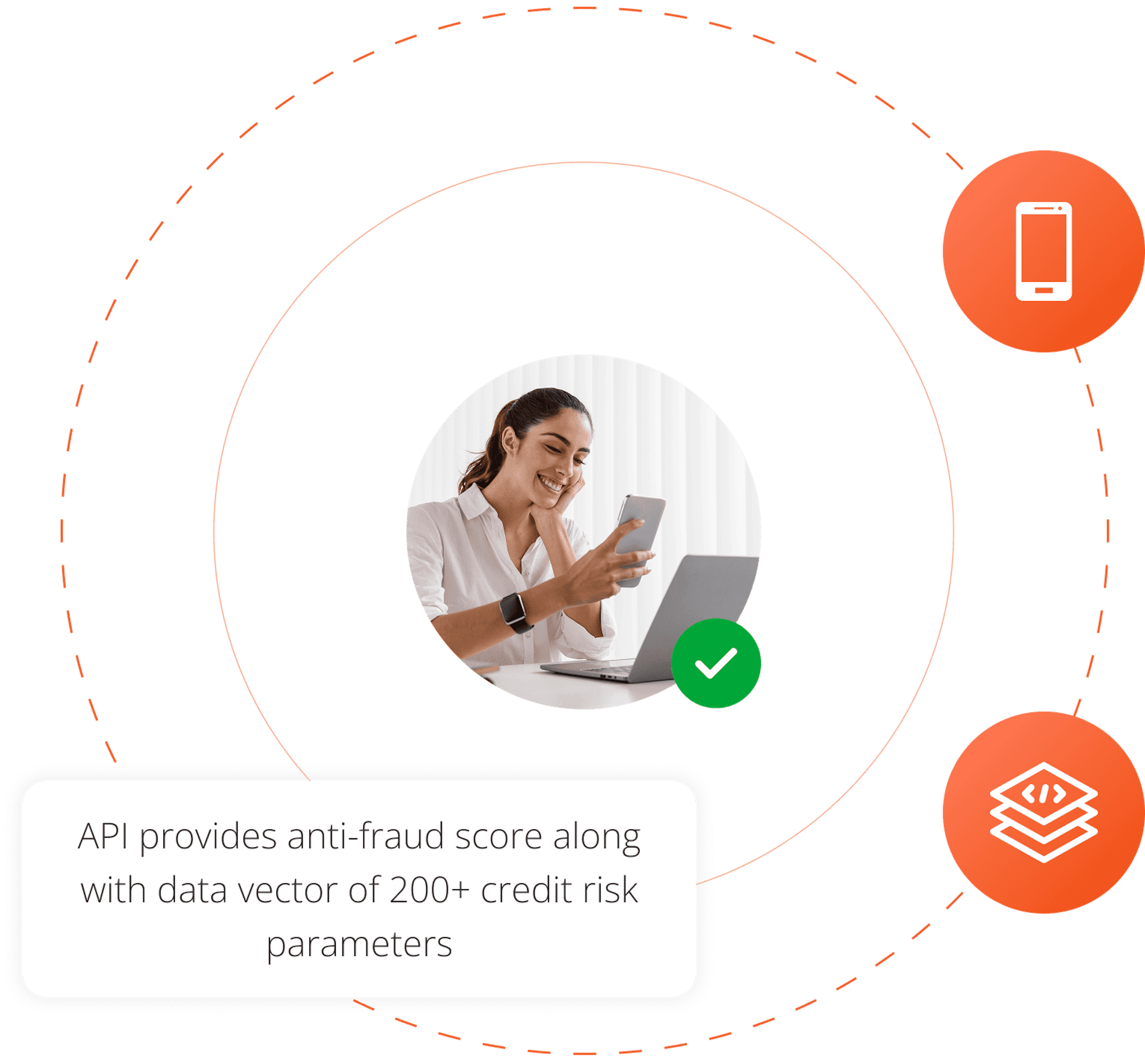
Device Data
Contains descriptors and anomalies related to device
Descriptors: detailed device type (mobile, tablet, desktop, etc), device manufacturer performance details (screen size, screen quality, RAM size, hardware characteristics)
Anomalies: screen geometry mismatch, screen resolution mismatch, etc
Device Software Data
Contains descriptors and anomalies related to software
Descriptors: operational system details, Browser details
Anomalies: various types of randomisers, session cloning, virtual machine, device routing markers, remote desktop tools
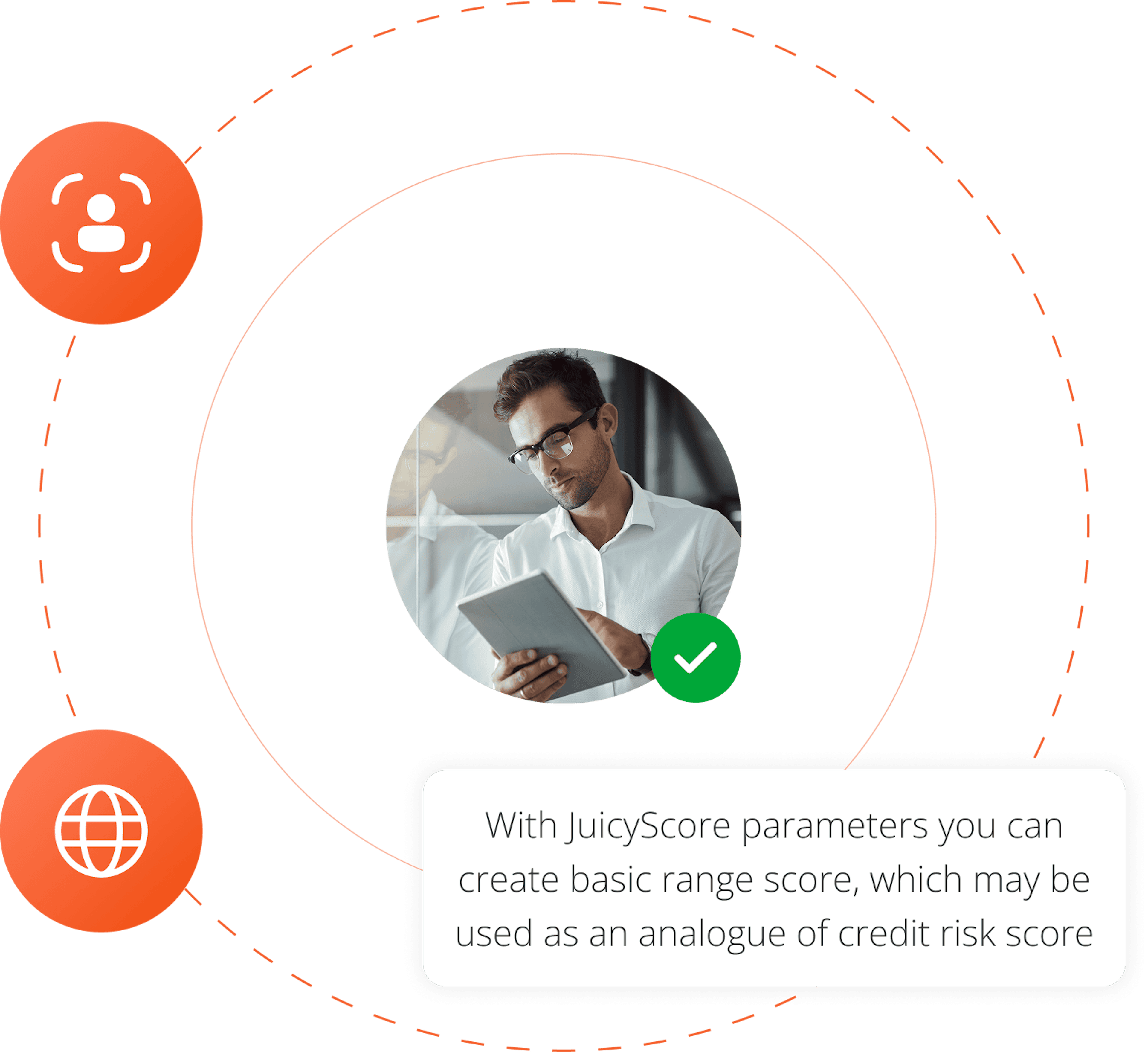
Behavioural Data
Contains frequency and behaviour parameters
Frequency: number of applications with the same device/user within last 1/7/30 days/ever, duplicated device
Behaviour: application fulfilment behaviour markers, way of contents reading, average speed of typing, flight time, dwell time.
Internet Connection Data
Contains descriptors and anomalies related to connection
Descriptors: real IPv4/IPv6, connection type, IP type, IP ageing, ISP
Anomalies: TOR, proxy, IP, time zone and DNS anomalies
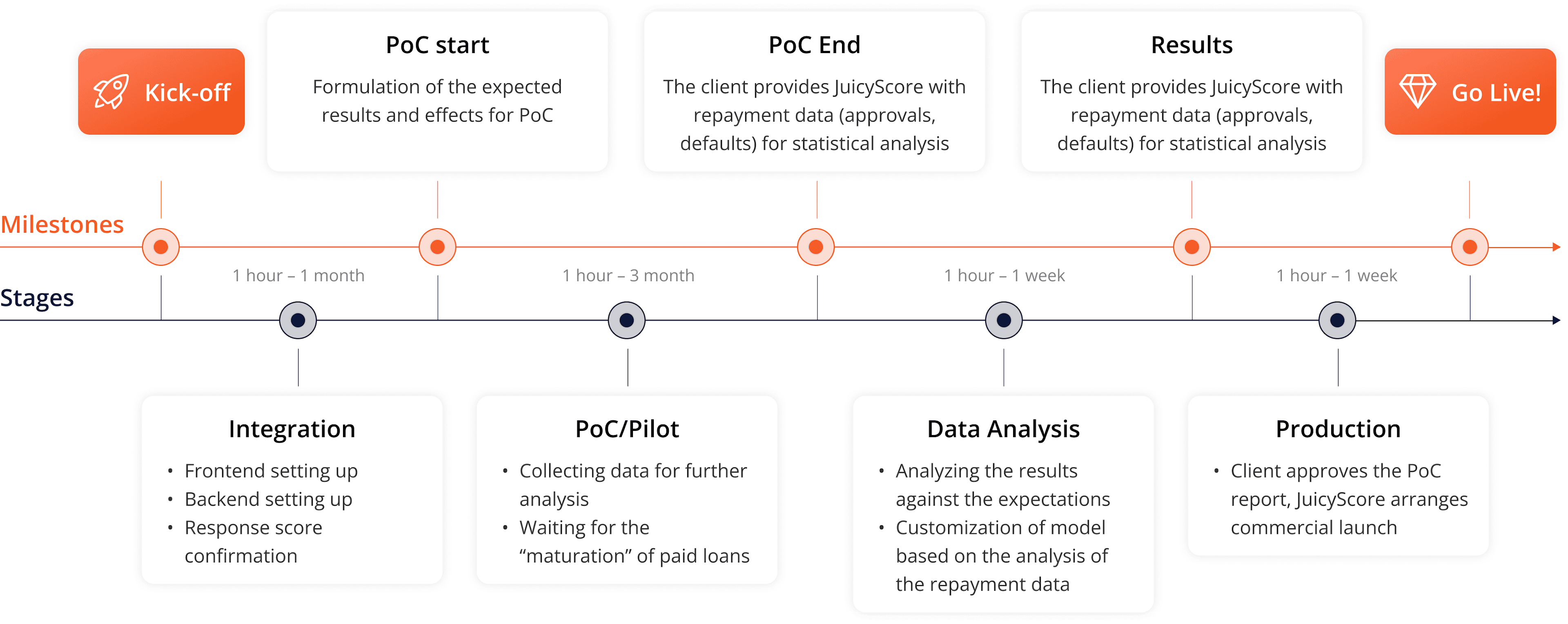
How it Works
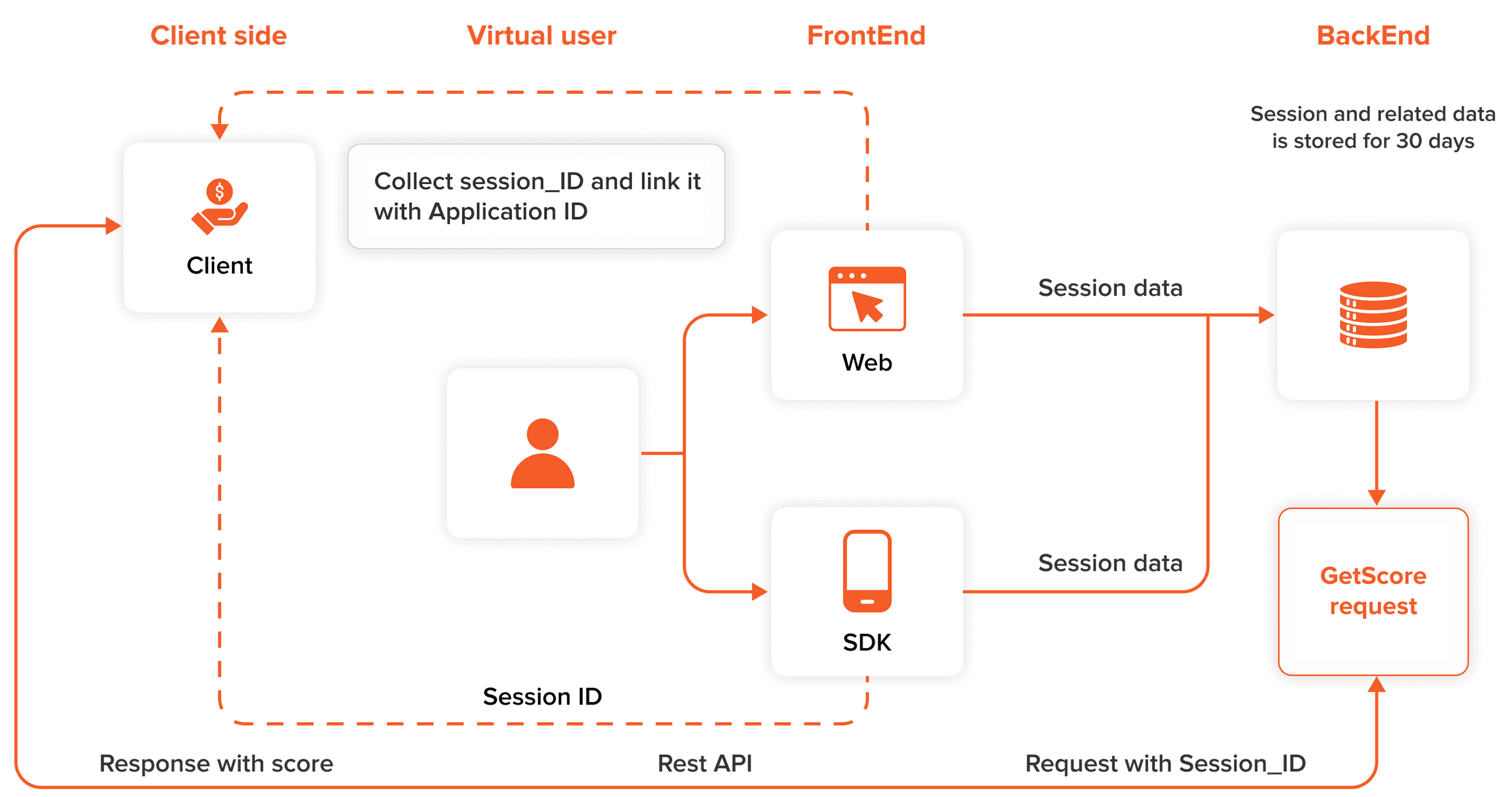
Our streamlined process is built on two key steps:
- 1
You send the Session ID with up to 65,000 varied parameters to the JuicyScore backend.
- 2
We provide a risk score and data vector based on the received data and applicable rules.
Designed with Data Protection from the Ground Up
Designed with Data Protection from the Ground Up
Our online scoring technologies are based on non-personal data, dynamic authentication, evaluation of disposable income, and other parameters. The bulk of the data that we collect is considered metadata, which translates to the data about the data. No personal data is ever collected or processed by JuicyScore or shared by our clients with us.
Only 1st party data
We are an embedded technology provider and process only the data we know works via our proprietary mobile and Web SDKs. We do not buy data from anyone.
Safety and Flexibility
Our clients can determine the set of non-personal data collected on their platforms by themselves. Any metadata containing information on applicants and devices collected on the financial institutions' platforms is deleted after 30 days unless our customers request us to delete the data at an earlier date.

See How We Spot Fraud Before It Happens — Book Your Expert Session
See It in Action with a Real Expert
Get a live session with our specialist who will show how your business can detect fraud attempts in real time.
Explore Real Device Insights in Action
Learn how unique device fingerprints help you link returning users and separate real customers from fraudsters.
Understand Common Fraud Scenarios
Get insights into the main fraud tactics targeting your market — and see how to block them.
Our Contacts:
Phone:+971 50 371 9151
Email:[email protected]
Leading Brands Trust JuicyScore:
Get in touch with us
Our dedicated experts will reach out to you promptly